Virtual LANs (VLANs) are a network segmentation technique that enables the creation of logically segmented networks within a physical network. A VLAN is a logical group of devices that can communicate as if they were on the same physical network, regardless of their actual physical locations. VLANs allow network administrators to group together devices that are not necessarily in the same physical location, improving network efficiency, security, and management.
VLANs are implemented at the data link layer (Layer 2) of the OSI model and are used to partition and manage broadcast domains within a local area network (LAN). A broadcast domain is a network segment in which all devices can receive broadcast packets sent by any other device in the same domain.
Key Features of VLANs
- Logical Network Segmentation:
- VLANs allow network administrators to create logical groups of devices that behave as if they are on separate physical networks, even though they may be connected to the same physical switches.
- Improved Network Security:
- VLANs help improve security by limiting the scope of broadcast traffic and restricting access between different VLANs. Devices in different VLANs cannot communicate with each other directly without routing through a router or Layer 3 device, enhancing security.
- Broadcast Domain Control:
- By creating smaller broadcast domains, VLANs help to reduce unnecessary broadcast traffic across the entire network, improving network performance.
- Simplified Network Management:
- VLANs simplify network management by allowing logical reconfiguration of devices and users without requiring physical rewiring of the network. Devices can be added, moved, or removed from a VLAN using configuration changes instead of physical moves.
- Support for Multicast Traffic:
- VLANs can be configured to efficiently support multicast traffic, which is used for applications like video conferencing and live streaming.
- Traffic Isolation:
- VLANs isolate traffic between groups of devices. For example, employees in the sales department can be placed in a separate VLAN from employees in the finance department, ensuring their traffic is isolated from each other.
How VLANs Work
VLANs work by tagging network frames with a VLAN ID. The IEEE 802.1Q standard is typically used for VLAN tagging, where a VLAN tag is inserted into the Ethernet frame header to indicate which VLAN the frame belongs to. This allows devices on different switches to identify the VLAN membership of a frame and forward it accordingly.
Here’s a simple example:
- Suppose a network has three departments: Sales, Marketing, and Finance.
- These departments are assigned three VLANs:
- VLAN 10 for Sales
- VLAN 20 for Marketing
- VLAN 30 for Finance
- Even though the devices in each department are connected to different physical switches, they can communicate as if they are part of the same network, thanks to VLAN tagging.
When a device sends a frame, the VLAN tag is added, indicating which VLAN the device belongs to. Switches use this tag to forward the frame only to the appropriate ports that belong to the same VLAN.
Types of VLANs
- Data VLAN (User VLAN):
- This type of VLAN is used for regular user data traffic. It is the most common VLAN type used in most networks, where user devices like computers, printers, and servers are placed. This VLAN handles general user traffic.
- Voice VLAN:
- A Voice VLAN is used specifically for voice traffic, typically for Voice over IP (VoIP) devices like phones and headsets. It helps prioritize voice traffic to ensure high-quality communication and reduce latency. Voice VLANs are often configured with Quality of Service (QoS) settings to give voice packets higher priority.
- Management VLAN:
- The Management VLAN is used for network management purposes. Network devices like switches, routers, and access points are placed in this VLAN for administrative access. It is isolated from user traffic to improve security and ensure that management traffic is not affected by heavy data traffic.
- Native VLAN:
- The Native VLAN is the default VLAN on a trunk port. In IEEE 802.1Q, trunk ports are used to carry traffic from multiple VLANs between switches. The native VLAN is used for untagged traffic on a trunk link, meaning that if a frame is sent without a VLAN tag, it is assumed to belong to the native VLAN.
- Default VLAN:
- The Default VLAN is VLAN 1. It is typically the factory default for switches and is used for switch management, although best practice recommends that VLAN 1 should be avoided for user data to improve security.
- Private VLAN (PVLAN):
- A Private VLAN is a special VLAN configuration used to isolate devices within the same VLAN. It is often used in scenarios where security is critical, such as in a data center, to prevent devices within the same VLAN from communicating with each other.
Advantages of VLANs
- Network Segmentation:
- VLANs allow networks to be segmented into logical parts, making them more manageable and secure. By isolating traffic, VLANs reduce the broadcast traffic that can cause network congestion.
- Improved Network Security:
- VLANs enhance security by allowing administrators to group sensitive devices together in a separate VLAN, thus isolating them from other users or devices. VLANs can prevent unauthorized access between segments of the network.
- Simplified Network Management:
- VLANs provide administrators with the ability to change network configurations without physically altering the network, making it easier to manage devices and services.
- Traffic Prioritization:
- With VLANs, certain types of traffic (like voice or video) can be prioritized over others, ensuring better performance for time-sensitive applications.
- Reduced Broadcasts:
- By reducing the size of broadcast domains, VLANs help to minimize the effect of broadcast storms, which can degrade network performance.
- Scalability:
- VLANs allow networks to scale easily as they provide logical grouping without the need for extensive physical network changes.
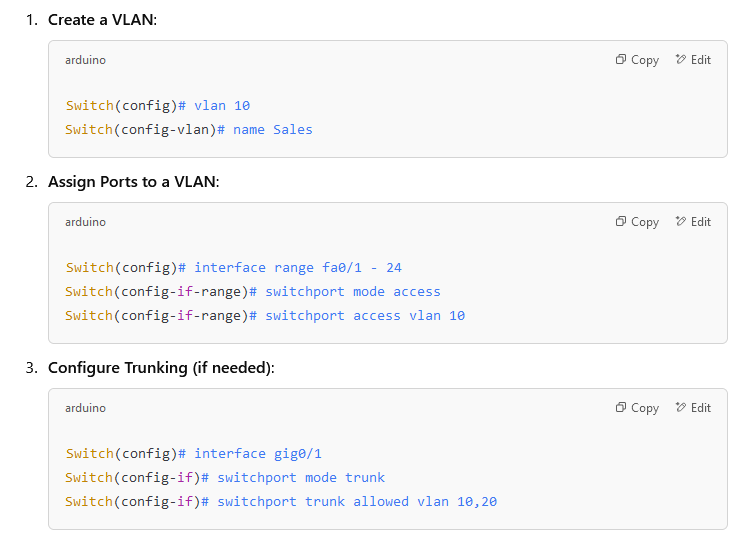
VLAN Configuration
VLAN configuration involves defining the VLAN IDs and assigning ports on a switch to the appropriate VLANs. The configuration also includes setting up trunking to allow VLANs to span multiple switches. Below is a basic configuration example for a Cisco switch
VLAN Tagging
VLAN tagging is essential for identifying and separating the traffic of different VLANs across switches. The IEEE 802.1Q standard defines the process of VLAN tagging, where a tag is inserted into the Ethernet frame. The tag includes the VLAN ID and other control information.
In VLAN tagging:
- Frames from VLAN 10 will have the VLAN ID of 10 in the header.
- Frames from VLAN 20 will have the VLAN ID of 20.
This ensures that switches can forward frames to the correct VLAN, even if the devices are physically connected to different switches.
VLAN Trunking
Trunking refers to the method of transmitting VLAN information between switches over a single link. A trunk link is a special type of network link that carries traffic for multiple VLANs. The most common protocol used for trunking is IEEE 802.1Q.
Trunk links use VLAN tags to identify which VLAN a frame belongs to, allowing multiple VLANs to be carried over a single physical connection.
Example of VLAN Setup
Consider a simple network with three departments: Sales, Marketing, and Finance. Each department will be assigned to a separate VLAN:
- VLAN 10 for Sales
- VLAN 20 for Marketing
- VLAN 30 for Finance
If the network is spread across multiple switches, trunking will be used to allow all VLANs to communicate across switches. Each switch port is configured to be part of a specific VLAN, and communication between VLANs will require a router or Layer 3 switch to perform routing between VLANs (inter-VLAN routing).
Disadvantages of VLANs
- Complexity:
- While VLANs simplify network management, they also introduce complexity, especially in large networks with many VLANs. Proper planning and configuration are needed to ensure the network operates efficiently.
- Routing Overhead:
- Communication between VLANs requires routing, which can increase network overhead. If many VLANs need to communicate frequently, the load on the router or Layer 3 switch increases.
- Increased Switch Configuration:
- VLAN configuration on switches can become time-consuming as the number of VLANs grows, requiring careful planning and management.
- Broadcast Issues in Large VLANs:
- VLANs still rely on broadcasts for certain operations, and a poorly designed VLAN network with too many devices in one VLAN can lead to broadcast storms and network congestion.
Conclusion
Virtual LANs (VLANs) are a powerful tool for network management, segmentation, and security. By logically grouping devices into separate broadcast domains, VLANs improve network performance, security, and scalability. Whether for a small business network or a large enterprise, VLANs help optimize resources, reduce unnecessary traffic, and provide a more secure and manageable network environment.
